Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Definitive Guide to Kubernetes Admission Controller
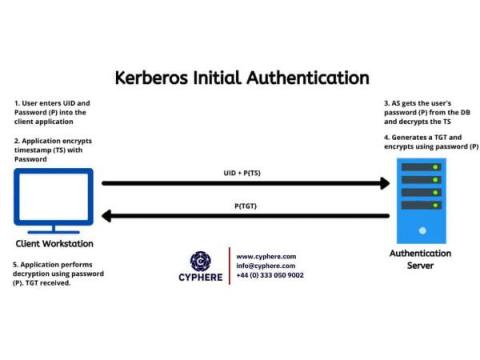
Kerberos Authentication: Basics to Kerberos attacks
Developed by MIT, Kerberos Authentication Protocol is the default authentication service for Microsoft Active Directory. It is named after the three-headed dog (Cerberus) found in Greek mythology, because the security protocol involves three major steps in the entire authentication process. Although Kerberos is a technology used by Microsoft Windows, by default, its implementations in other operating systems, such as Linux, FreeBSD and macOS, are also present.
Signs Your Cyber Loss Control Isn't Working
Most cyber insurance policies include a form of value-added service meant to help policyholders avoid cyber incidents. These services create differentiation in the market for insurers and help the bottom line. In fact, a recent survey of cyber insurers found that risk engineering services are a bigger driver of profitability than underwriting accuracy. Yet, we know that the dynamic nature of cyber risk has insurers struggling to keep up and new approaches to evaluating that risk are needed.
Data Eats the World: You'll Consume It Intelligently with the Autonomous SOC
“Software is eating the world.” That phrase entered the high-tech lexicon in 2011, courtesy of Marc Andreessen, co-founder of both Netscape and venture capital firm Andreessen Horowitz. His thesis is proven time and again. If you substitute data for software, it amplifies the power of Andreessen’s observation. Consider the following statistics on how much data is created every day: Technology users alone generate more than 1.145 trillion MB of data every day!
Securing SSH on EC2: What are the real threats?
Every compliance audit will ask you to secure SSH, and every time a scanner checks the configuration or CSPM of your cloud account you’ll be warned for it. For example, if you don’t secure SSH on EC2, you’ll certainly get a critical alert stating that one of your Security Groups has its SSH port (22) open to the world. When this happens, you may think: Have I been pwned?
4 ways financial services leaders can stay ahead of the cybersecurity risk curve
With Trustwave, the Best in MDR Just Got Better
Trustwave has recreated new Managed Detection and Response (MDR) services to deliver unmatched capabilities tailored to fit an organization regardless of size or budget. While larger organizations may have the resources for heavy security investments, small and medium enterprises (SME) often struggle to keep up with this punishing pace and finding enough qualified security personnel can be even more challenging with the ongoing skills shortage.
Security Tips as Summer Travel Heats Up
“Safe travels!” It’s been a long time since most of us have uttered that phrase. Now we’re saying it with increasing regularity as family members, friends and colleagues are traveling again with greater ease and confidence. I’d like to suggest that when those of us in the security industry wish someone a safe trip, we use the opportunity to remind them of the increased cybersecurity risk they now face and share our expertise for how to protect themselves.
Cybercriminals are exploiting cryptocurrency donations to the Ukraine crisis
Our threat intelligence recently shared several threats they’ve uncovered through monitoring our B2B platform, in our recent report: Keeping pace with emerging threats: Summer 2022 roundup. One of the standout threats to keep your users aware of is a group of phishing emails impersonating Ukrainian charitable appeals – specifically those requesting cryptocurrency donations.