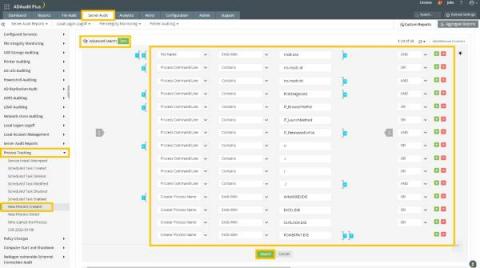
How ADAudit Plus helps you assess your exposure to Follina (CVE-2022-30190)
The recently discovered Windows zero-day vulnerability continues to make news as threat actors across the globe are relentless in their efforts to exploit it. The vulnerability, dubbed Follina, can be exploited when the Microsoft Support Diagnostic Tool (MSDT) is called by a Microsoft Office application using the URL protocol.