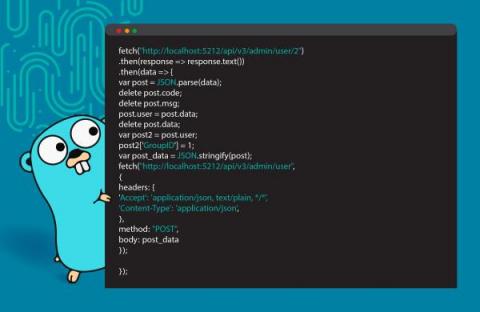
8 Ways Indian Organizations Can Mitigate Cyber Threats
Global cybersecurity is becoming more reliant on using advanced, more complex safety mechanisms to resolve vulnerabilities. Governments and businesses worldwide struggle to safeguard their data and networks and prevent future crises. At the same time, cyber threats are becoming just as complex. With each new step in cybersecurity innovation, cyber threats also gain momentum, eventually posing major security challenges for governments.