Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
New in Vanta | October 2023
This past month, we announced the single destination to showcase your security posture, Vanta Trust Center, 19 new integrations, Private Links for Vendor Risk Management, and more:
Significant Changes from NIST SP 800-53 rev4 to rev5
The National Institute of Standards and Technology has introduced a new revision of the Special Publication 800-53, revision 5. As with any document change of this scope there are minor and major changes. This paper will provide a high level overview of the significant changes, addressing a redefined focus in control families, accountability, governance, as well as a discussion of new control families, privacy transparency and supply chain risk management.
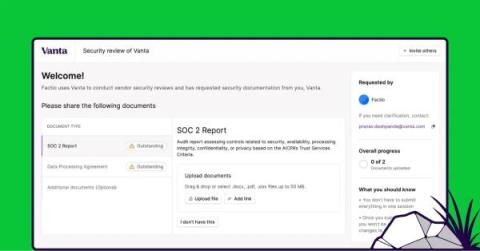
Introducing Private Links: A faster, easier way to gather vendor security information
When it comes to conducting vendor security reviews, the two most time-consuming tasks are gathering the relevant information from your vendor and analyzing it thoroughly. Last month, we announced AI-powered security document analysis to drastically simplify the process of extracting insights from SOC 2 reports, DPAs, and other sources that document a vendor’s security posture.
How to Choose Right PCI SAQ for Your Business
In the world of digital transactions, businesses handling payment cards must demonstrate their data security measures through the Payment Card Industry Self-Assessment Questionnaire (PCI SAQ). Completing the SAQ is a key step in the PCI DSS assessment process, followed by an Attestation of Compliance (AoC) to confirm accuracy. Level 1 merchants and service providers, mandated by PCI SSC or customers, must complete a Report on Compliance (RoC), while others use an SAQ.
GitOps - Enhancing security and ensuring compliance in Kubernetes deployments
Less than half of UK businesses have strong visibility into security risks facing their organisation
Elevate Trust and Transparency with Vanta Trust Center
Strengthening Cyber Defenses with Multi-Factor Authentication
The need for robust cyber defenses has never been more prevalent. We live in a world where remote access to data is the norm, opening up additional vulnerabilities when protecting digital assets. Additionally, organizations need to comply with data privacy requirements including understanding Digital Personal Data Protection. Mutli-Factor Authentication (MFA) isn’t a new concept. However, despite this, there is still confusion surrounding the mechanism and how it adds to cyber defense.
Introducing Vanta Trust Center and the State of Trust Report
Today we’re thrilled to introduce Vanta Trust Center, a centralized source of truth for companies to showcase their security posture confidently. Following Vanta’s acquisition of Trustpage earlier this year, Trust Center combines the capabilities of Trustpage Trust Centers and Vanta Trust Reports, making it easier than ever for customers to automatically manage their workflows and accelerate the security review process — all from within Vanta.