Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Preventing insecure deserialization in Node.js
Serialization is the process of converting a JavaScript object into a stream of sequential bytes to send over a network or save to a database. Serialization changes the original data format while preserving its state and properties, so we can recreate it as needed. With serialization, we can write complex data to files, databases, and inter-process memory — and send that complex data between components and over networks.
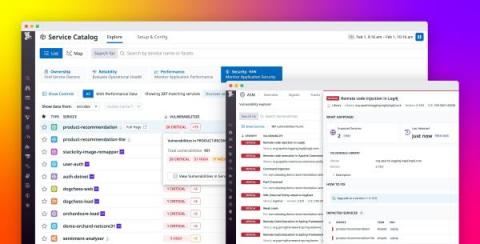
Gain visibility into open source vulnerabilities with Datadog Application Vulnerability Management
Open source libraries have become an indispensable part of modern applications. Approximately 90 percent of organizations use open source software to support their services, but monitoring these dependencies can be difficult when environments run thousands of ephemeral services.
What is Vulnerability Management?
Vulnerability management refers to continuously identifying, reporting, and remediating security risks within the cyber assets from networks to cloud platforms. It becomes vital that good cyber security measures with an extensive vulnerability management system be placed to ensure data and application safety.
Does HIPAA require penetration testing?
The HIPAA Security Rule requires healthcare organizations to perform regular security risk assessments to protect e-PHI. Penetration testing can help organizations with this requirement.
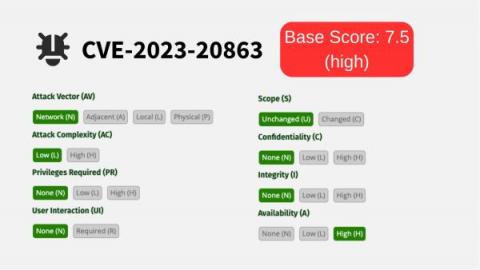
Another Expression DoS Vulnerability Found in Spring - CVE-2023-20863
Developer-centric DAST with Bright Security
Security testing is increasingly viewed as an essential part of the software development lifecycle (SDLC). Traditionally, agile software development has focused on development velocity, rapid market feedback, and delivering high quality products and services. However, software that's vulnerable to cyber attacks is not valuable to end users and creates huge risks for both customers and software vendors. This makes it critical to integrate security testing into the software development process.
Prepare for Zero-Day Threats in Your Supply Chain
Leading cybersecurity experts Major General John F. Wharton, (US Army ret); Oleg Strizhak, Shell’s Digital Supply Chain Risk Manager; and Sam Curry, the CISO of Zscaler, recently sat down with SecurityScorecard’s President of International Operations Matthew McKenna to discuss how organizations can prepare themselves and their supply chains for zero-day attacks as well as best practices for supply chain risk management.
What Is Zerologon and How Do You Mitigate It?
Commonly referred to as Zerologon, CVE-2020-1472 is the Common Vulnerabilities and Exposures (CVE) identifier assigned to a vulnerability in Microsoft’s Netlogon Remote Protocol (MS-NRPC). MS-NRPC is essential for authentication of both user and machine accounts in Active Directory.
CVE-2023-29383: Abusing Linux chfn to Misrepresent /etc/passwd
A little bit of background for those not familiar with chfn… “chfn (change finger) is used to change your finger information. This information is stored in the /etc/passwd file and is displayed by the finger program.