Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Security implications of HTTP response headers
When a web server receives an HTTP request, it is processed and sent back with a response containing the requested resource and any additional information in the form of HTTP response headers. These headers provide important data, such as last-modified dates, content types, and cache-control settings. The browser then uses this information to determine how to display or store that particular resource. This process helps ensure efficient communication between web servers and browsers.
Can AI write secure code?
AI is advancing at a stunning rate, with new tools and use cases are being discovered and announced every week, from writing poems all the way through to securing networks. Researchers aren’t completely sure what new AI models such as GPT-4 are capable of, which has led some big names such as Elon Musk and Steve Wozniak, alongside AI researchers, to call for a halt on training more powerful models for 6 months so focus can shift to developing safety protocols and regulations.
Microsoft Power Platform DLP Bypass Uncovered - Finding #4 - Unblockable connectors
Hello everyone! I’m Yuval Adler, Customer Success Director at Zenity. I’m inviting you to read my blog series where I share new Microsoft Power Platform DLP Bypass findings we’ve uncovered.
API3:2019 Excessive Data Exposure: Understanding the Risks, Impacts, and How to Prevent It
Three New BGP Message Parsing Vulnerabilities Disclosed in FRRouting Software
In our new vulnerability research report, Forescout Vedere Labs discusses an often-overlooked aspect of Border Gateway Protocol (BGP) security: vulnerabilities in its software implementations. More specifically, vulnerabilities in BGP message parsing found in the popular FRRouting implementation that could be exploited by attackers to achieve a denial of service (DoS) condition on vulnerable BGP peers.
CyRC Vulnerability Advisory: CVE-2023-25826 and CVE-2023-25827 in OpenTSDB
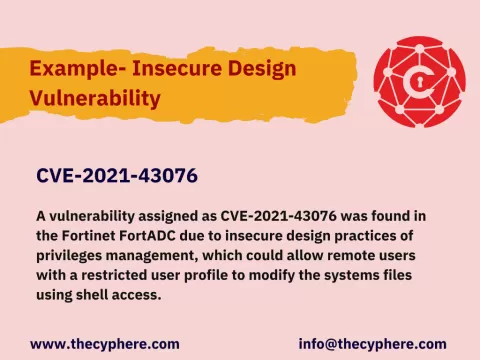
Insecure design vulnerabilities - what are they, and why do they occur?
The Total Guide On CVSS (Common Vulnerability Scoring System)
CVSS or Common Vulnerability Scoring System is a framework that numerically characterizes the severity of software vulnerabilities between the range of 0-10. CVSS scores help infosec organizations with vulnerability management and prioritization of vulnerabilities for efficient remediation.
What Is A Vulnerability Report?
A vulnerability report is a document provided by security testers after the assessment of a target’s security. It contains a detailed analysis of the vulnerabilities uncovered along with the test cases run during the assessment. The report also provides possible remedial steps.