Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Identifying beaconing malware using Elastic
The early stages of an intrusion usually include initial access, execution, persistence, and command-and-control (C2) beaconing. When structured threats use zero-days, these first two stages are often not detected. It can often be challenging and time-consuming to identify persistence mechanisms left by an advanced adversary as we saw in the 2020 SUNBURST supply chain compromise. Could we then have detected SUNBURST in the initial hours or days by finding its C2 beacon?
Investigate Log4Shell exploits with Elastic Security and Observability
Following the discovery of Log4Shell, a vulnerability in Log4J2, Elastic released a blog post describing how users of our platform can leverage Elastic Security to help defend their networks. We also released an advisory detailing how Elastic products and users are impacted.
Linux malware protection in Elastic Security
With our recent 7.16 Elastic Security product release, we improved our existing Linux malware feature by adding memory protection. In this blog, brought to you by Elastic’s Engineering Security Team, we lean into this recent advancement to show how we are protecting the world’s data from attack.
Devo's 2022 Cybersecurity Predictions: Part Three
In part two of our 2022 cybersecurity predictions series, Devo Security Engineering Director Sebastien Tricaud explained Web3 and new security testing trends. While cybersecurity tools and approaches are certainly evolving quickly, so are cybercriminals. Here are my insights on cyberthreats and attacks we should expect to see more of this year.
How IHG modernized SecOps during the pandemic
Is a SIEM Right For You?
Security Information and Event Management (SIEM) is the combination of Security Information Management (SIM) and Security Event Management (SEM) systems. SEM systems store and interpret logs for real-time security event analysis which enables quick defensive action. SIM systems collect data for trend analysis and provide automated reporting. By combining these two technologies together, a SIEM provides rapid identification, analysis, and recovery from security events.
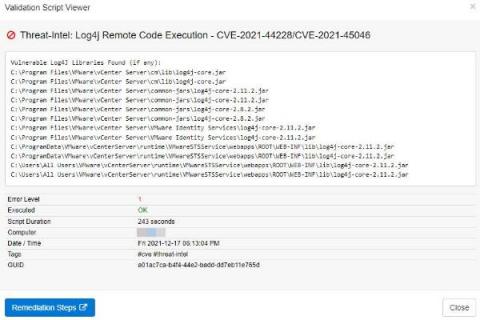
Discovering vulnerable Log4J libraries on your network with EventSentry
Just when the Microsoft Exchange exploit CVE-2021-26855 thought it would win the “Exploit of the year” award, it got unseated by the – still evolving – Log4J exploit just weeks before the end of the year! Had somebody asked Sysadmins in November what Log4J was then I suspect that the majority would have had no idea. It seems that the biggest challenge the Log4J exploit poses for Sysadmins is simply the fact that nobody knows all the places where Log4J is being used.
EventLog Analyzer year in review: 2021
Our log management solution, EventLog Analyzer, has had yet another busy year. Being named in the 2021 Gartner Magic Quadrant for SIEM for the fifth time was one of the high points. We also had the satisfaction of helping many organizations ensure their overall cybersecurity health with new features to meet evolving demands. Our journey in 2021 With many organizations adopting hybrid work models over the last year, there was a steady increase in the volume and severity of cyberattacks.
Devo's 2022 Cybersecurity Predictions: Part One
There’s only one thing that’s certain in cybersecurity: The cyberthreat landscape is constantly changing, and the tools and solutions we have at our disposal to combat cybercrime must continue evolving if we are to stay ahead of — or at least keep up with — them. As 2021 winds down, the Devo security team is already looking ahead to the most pressing cybersecurity trends likely to appear in 2022. Here are my top three predictions for the new year.