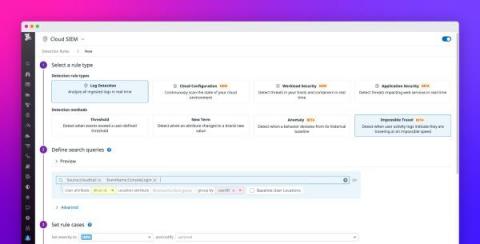
Elastic Security 8.1: Stop novel attacks in their tracks
With the release of Elastic Security 8.1, enhance defenses against novel attacks like Log4Shell and prevent adversaries from compromising macOS systems. Achieve visibility into host-based network activity, leverage new sources of threat intelligence, collect data from across your enterprise, and more. Let’s jump in.