Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Top Security Information and Event Management Use Cases
Cyber security threats and measures mandated by regulations require an advanced security solution for organizations. Many reasons, such as false positives, difficulty in budget control, vulnerable protocols, and misconfigurations, can be confusing when choosing the right security solution. In order to get rid of all these concerns, security information and event management (SIEM) solutions come to the fore as solid and centralized security platforms.
Elastic and Tines partner to detect security threats and reduce mean time to respond
Today, we’re happy to announce that Elastic and Tines are partnering to help our joint users detect security threats and reduce mean time to respond. Many of the world’s best security teams rely on the power of Elastic’s high-speed, cloud-scale detection, prevention, and response capabilities to investigate and contain potential security threats within their environments.
Shell Evasion: An Insider Threat
Cybersecurity strategies within cloud environments are often seen as a complicated landscape with rapidly developing technologies, architectures, and terms. Simultaneously, there are continuously motivated individuals and groups trying to utilize vulnerabilities for illicit uses such as to increase access to the data, install malware, disrupt services, and more.
Deep dive on the BLISTER loader
Yesterday, the Elastic Security Research Team released a detailed report outlining technical details regarding the BLISTER launcher, a sophisticated campaign that we uncovered in December 2021. This latest release continues on research we’ve developed while observing the campaign over the last few months — specifically pertaining to the technical details of how the group behind this payload is able to stay under the radar and evade detection for many new samples identified.
Is It Reasonable to Deploy a SIEM Just for Compliance?
Many organizations need to meet various compliance standards, and investing in a security information and event management (SIEM) solution can often help them reach that goal. But it worth the cost and effort to deploy a SIEM solution solely for compliance? Or is there a way to maximize the value of your SIEM by strengthening cybersecurity as well as achieving compliance? This article will help you answer those critical questions.
In Cybersecurity, AI is Not A-OK
Artificial intelligence has been (and continues to be) a popular topic of discussion in areas ranging from science fiction to cybersecurity. But as much fun as it might be to discuss my favorite sci-fi AI stories, let’s set aside the works of Asimov, Bradbury and other storytellers to focus on the role of AI in cybersecurity.
What's new in Elastic Security 8.2: Streamline analyst workflows with context and expertise
Elastic Security 8.2 powers the efficiency and effectiveness of security teams, arming analysts with invaluable insights and deep visibility into the attacks targeting their organization. The release delivers rich alert contextualization, osquery host inspection directly from an alert, new investigation guides, and the general availability of threat intelligence. Let’s jump in.
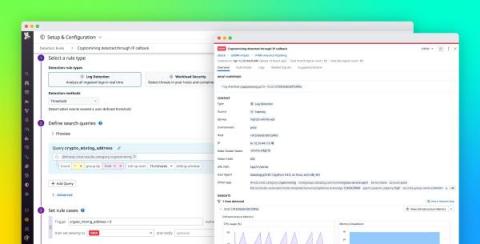
Detect cryptocurrency mining in your environment with Datadog Cloud SIEM
Cryptocurrency mining (or crypto mining) can be a lucrative yet resource-intensive operation, so cyber threat actors are targeting more organizations in order to take advantage of their cloud resources for mining. Datadog Cloud SIEM can now help you monitor your cloud-based systems for unwanted crypto mining via a built-in detection rule. All you need to get started is to configure your resource logs with Datadog’s @network.client.ip standard attribute.
Detect Credential Access with Elastic Security
Within our Elastic Security research group, a strong area of focus is implementing detection mechanisms for capabilities we understand adversaries are currently exploiting within environments. We’ll often wait to see the impact that bringing these capabilities to market will have from a detection standpoint. This allows our researchers to explore different detection strategies through these additions, providing deep insight into how effective the Elastic Security platform can be.