Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Making a Business Case for the Right SIEM
Let’s admit it — switching to a new SIEM can be tough. And expensive. But even when it isn’t tough or expensive, it’s always scary.
Why end-to-end visibility is critical to secure your apps in a serverless world
SciSec Team Applies Creativity, Curiosity and Innovation to Help Security Teams Work Smarter and Protect Organizations from Threats
Today Devo announced Devo SciSec, which brings together a talented team of threat research, advanced data science, and machine learning experts under the leadership of CTO Gunter Ollmann to help our customers preemptively detect and mitigate entire classes of threats. See and hear what Gunter has to say about SciSec in this video. Even before their formal introduction, the SciSec team has been busy delivering value-added capabilities to Devo customers.
Sumo Logic expands Cloud SIEM security coverage for Microsoft Azure
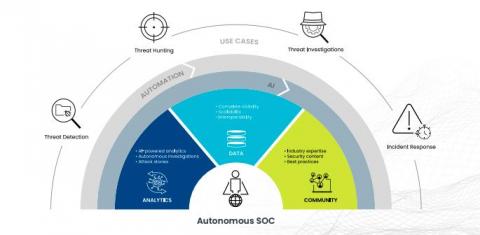
Emerging Technologies and Evolving Analysts Are Giving Rise to the Autonomous SOC
Fueled by the need to detect new, emerging threats while supplying meaningful feedback upstream to anticipate and prevent future ones, the modern SOC is the engine that protects organizations worldwide. The heart of that engine is common to all SOCs since they debuted more than a decade ago: people.
How to Use SIEM Tools in the Modern World
In our highly connected world, organizations of all sizes need to be alert to the risk of cyberattacks. The genuine threats to today’s enterprises include data leaks, ransomware, and theft of commercial secrets or funds, with the potential for severe financial and reputational damage. Investing in tools to monitor your systems and alert you to suspicious activity as early as possible is vital for strengthening your security posture.
6 cybersecurity must-haves for innovative public sector leaders
ThoughtLab’s newly released cybersecurity benchmark study revealed that cybersecurity is at a critical inflection point across industries.
Public Sector Demand for Devo Solutions Leads to New Partnerships & Contracts
Following our February announcement that Devo has been designated as FedRAMP “In-Process,” I’m excited to report that our public sector momentum continues in other key areas. Here are some recent highlights: All of this momentum and growth is an affirmation of the excellence of the Devo Platform and the exceptional quality of our success services to support them. And it also demonstrates Devo’s long-term commitment to serving our customers and partners in the public sector.
A peek behind the BPFDoor
Threats knock on your door all the time. In this research piece, we explore BPFDoor — a backdoor payload specifically crafted for Linux in order to gain re-entry into a previously or actively compromised target environment. This payload has been observed across systems for five years, suggesting that the threat actors responsible for operating the malware have been around for some time and have likely operated undetected in many environments.