Advancing SBOM standards: Snyk and SPDX
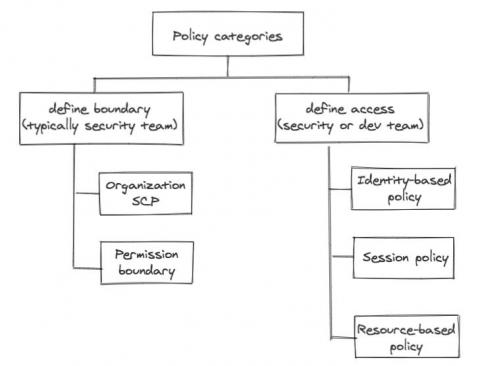
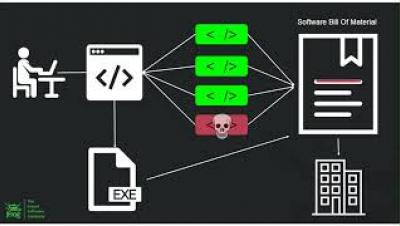
Many people will have heard of the SPDX project through the work on the SPDX License List. This list of canonical identifiers for various software licenses is used in a huge range of developer-focused software, from Snyk to GitHub. But the SPDX project, which is part of the Linux Foundation, has a much broader focus on providing an open standard for communicating software bill of material information.