Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
July 2022
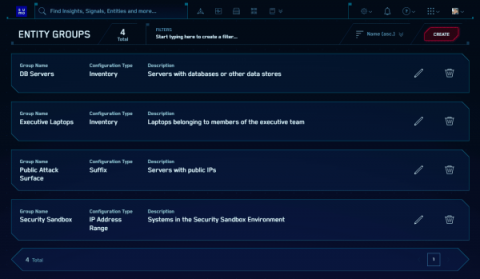
Use new Cloud SIEM Entity Groups to make threat response more efficient
AWS-ome News for Devo and Our Customers
I am very pleased and proud to share the big news that Devo is now an AWS Security Competency Partner. This is a significant milestone for Devo and it’s important for our current and future customers and partners. This designation validates that Devo has successfully met AWS’s technical and quality requirements for providing customers with a deep level of expertise in threat detection and response.
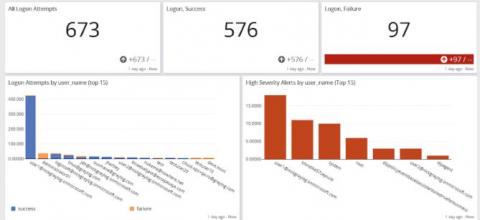
Enhance Your Devo Data Search Capabilities with Stat Counts
With today’s expanding attack surfaces and the growing sophistication of adversaries, exploding volumes of data are negatively affecting SOC teams’ success. According to the 2021 Devo SOC Performance Report, 67% of respondents said their lack of visibility into the attack surface makes working in the SOC painful.
3 Important German BSI Documents Every SIEM & SOC Manager Needs To Know About
The German IT Security Act 2.0 (IT-SiG 2.0) has been in force since May 2021. Due to this new law, significantly more German companies have been classified as operators of critical infrastructures (KRITIS) than ever. This is a major cause of headaches for many managers. In addition, IT departments are starting to ask themselves: "Are we now regarded as KRITIS"? And if so, "What do we have to take into consideration?"
RHONDOS and Devo Partner to Secure Organizations' Business-Critical SAP Data
RHONDOS is proud to have established a strategic partnership with Devo, the only cloud-native logging and security analytics platform. RHONDOS is bringing PowerConnect for SAP to Devo, and together we will provide mutual customers with an all-in-one solution so they can confidently address the question of what to do with SAP data.
Selecting SIEM Tools - Questions to Consider
The Role of Community in the Journey to the Autonomous SOC
No security team — at least no effective security team — can operate successfully in a silo. Even expert teams know the value of leveraging the power of the community to build effective security content, share intelligence, and keep current with best practices.
New 1Password SIEM integration with Sumo Logic and Panther
Reduce the time your team spends investigating security issues by using a customizable dashboard that shows your organization’s entire security posture. With the new Sumo Logic and Panther integrations for 1Password, you can monitor potential risks around company data or credentials stored within 1Password.
geeks+gurus: SOAR: SOC Automation at its finest
geeks+gurus: Cloud Migration
End to End Incident Response Using Elastic Security
5 Telltale Signs You're Running a Cloud-Hosted - not a Cloud-Native - SIEM
The necessity of a SIEM for organizations and their security teams has evolved dramatically over time. It has gone from edge use cases and compliance to the current form of threat detection, incident response, and threat hunting. As the use cases have changed, so has the architecture. As a result, organizations that have been quite familiar with running their SIEM on-premises are now looking for modern architectures to reduce the workload on their analysts. The simple choice: SaaS, of course.
Are your credentials safe? Decoding credential phishing attacks
Companies have increasingly allowed bring your own device (BYOD) policies to support remote work, but in today’s cybersecurity landscape, this trend has led to an increased attack surface. Each additional endpoint increases the potential for credentials to be compromised through credential phishing attacks. Hackers are leveraging this trend to conduct insider attacks, leaving businesses vulnerable to data breaches.