Web Shell Upload Via Extension Blacklist Bypass - Part 1
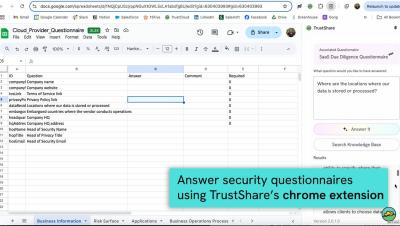
We delve into an in-depth exploration of a common web security vulnerability related to file uploads and it demonstrates how attackers can exploit weaknesses in file extension blacklists to upload malicious web shells. We also cover the mechanics of bypassing these security measures, including specific techniques and tools used to see practical examples of how to conduct such an attack in a controlled environment, emphasizing the importance of understanding these vulnerabilities for defensive programming.