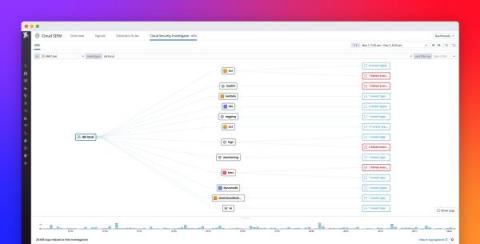
How Graph-powered SSPM Adds the Right Context
SaaS apps have become the “easy button” for organizations seeking a fast and simple way to make foundational business apps available to their employees. According to Gartner, “SaaS remains the largest public cloud services market segment, forecasted to reach $176.6 billion in end-user spending in 2022,” growing 14% over 2021.