Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2022
Use Keeper Connection Manager to Automatically Discover & Connect to AWS EC2 Instances
One of the selling points of cloud computing is the ability to quickly spin up new machines as needed. Unfortunately, this means that cloud environments grow very complex, very quickly – and manually updating configuration files to add new instances gets really old, really fast. It’s easy to make a mistake, which inhibits productivity and causes security issues, especially when accessing machines remotely.
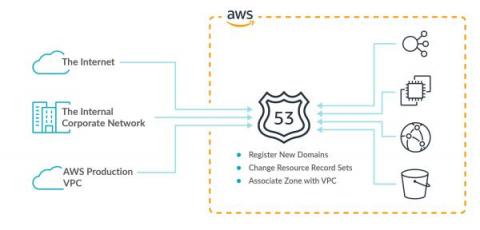
How to Secure AWS Route 53 with Sysdig
Either through human error or intentionally, configuration changes in the cloud may suddenly increase your attack surface. AWS Route 53 is an example of a service that needs to be continuously tracked for risky changes. As the first line of defense of our cloud, it is necessary to secure Amazon Route 53 and monitor risky configuration changes to avoid unwanted surprises. As you probably know, AWS Route 53 is of course a very popular DNS service offered by AWS, with millions of top-level domains.
AWS Security Best Practices
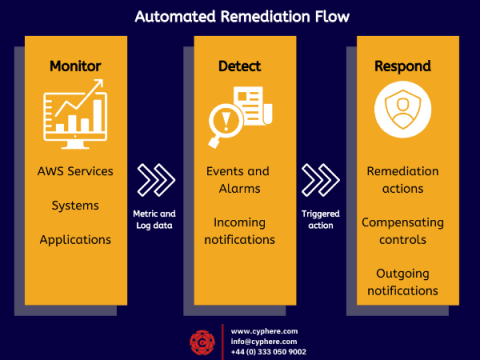
Using security best practices helps businesses establish a security baseline and protect their AWS infrastructure from potential risks. By implementing these practices, companies can reduce the likelihood of data breaches, leaks, and other threats. Additionally, using security best practices can help businesses detect and respond to threats more quickly and effectively.
What is SaaS Application and How to Secure it?
Cloud technology is a booming sector in today’s digital world. The business environment is trying to make the most of it from cloud-based platforms. With pandemics striking the globe, cloud applications have come to rescue business operations from remote locations. It improves connectivity and accessibility irrespective of the location. However, every technology has its advantages as well as disadvantages.
SMB Guide to Cloud Security
Like their larger counterparts, small- and medium-sized businesses (SMBs) are moving swiftly to migrate IT workloads to the cloud, hoping to slash operating costs, eliminate technical debt, and accelerate digital transformation projects. However, cloud migration security risks are often poorly understood at the outset or overlooked entirely.
What is Cloud Security Posture Management (CSPM)?
Businesses are moving their data to the cloud to reduce costs and increase their agility. As more applications and data migrate to the cloud, the risk of sensitive data and applications being exposed dramatically increases. In addition, as organizations deploy applications and services in different cloud environments, maintaining security and compliance across the board is becoming more complex than ever before.
Setting Up Azure with SSO Connect Cloud
11 Questions You Should Ask About Your Cloud Security
The world is becoming more digital with each passing day. Many companies are trying to transition to an online or to a hybrid system, where they can offer flexibility and autonomy to employees and have a more efficient way of managing their day-to-day operations. The digital transformation to the online world requires businesses to invest in cloud computing and cloud security software.
Staying Connected with Cloud Exchange: Netskope Cloud Threat Exchange & Digital Shadows Plugin
Many technology professionals have experienced the sense of frustration that occurs when multiple tools in their environment do not play nicely with each other. When technology leaders are making decisions about bringing new tools into their environment, they should be thinking about more than whether the platform is just a shiny new object that adds a new capability to their team.
SSE: Mitigating the Risks in Moving Data to the Cloud w/ Jim Dolce, Chairman & CEO at Lookout
How To Identify and Stop a Phishing Attack
Phishing is a real problem. One that can wreak havoc on your digital and financial life. Here, we’ll look at different ways we can identify a phishing scam and stop it in its tracks. Phishing is the practice of sending emails (or other messages) with the intent to make the recipient believe it’s from a certain company or individual.
Market Trends And Predictions For 2022
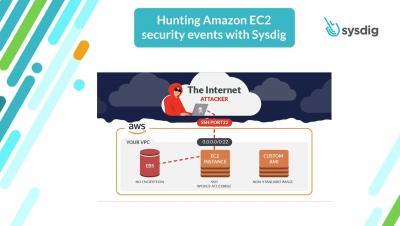
How to Secure Amazon EC2 with Sysdig
Enforcing Cloud Resource Policy Guardrails for HashiCorp Terraform Cloud
I’m excited to announce the Styra DAS integration with HashiCorp Terraform Cloud via run tasks is now generally available to Styra DAS users! Users can now enforce cloud resource policy guardrails at every step of the DevOps process, including right before Terraform Cloud applies changes to your cloud resources.
Netskope - Security That's Ready for Anything
What Are Web Cookies? The Privacy and Security Risks of Internet Cookies
This article has nothing to do with chocolate chips or sprinkles. Sorry about that. Instead, we're talking about computer cookies and how too many web cookies can be bad for your online health. While cookies are enormously helpful and necessary for an easy-going web experience, they are not all good, and many pose some genuine privacy concerns. But what is a cookie, how does one work, and how do they (sometimes) infringe on your digital rights?
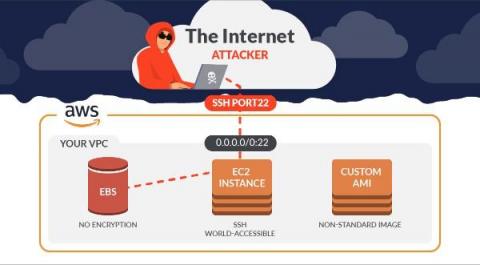
Securing SSH on EC2: What are the real threats?
Every compliance audit will ask you to secure SSH, and every time a scanner checks the configuration or CSPM of your cloud account you’ll be warned for it. For example, if you don’t secure SSH on EC2, you’ll certainly get a critical alert stating that one of your Security Groups has its SSH port (22) open to the world. When this happens, you may think: Have I been pwned?
Securing cloud workloads in 5 easy steps
As organizations transition from monolithic services in traditional data centers to microservices architecture in a public cloud, security becomes a bottleneck and causes delays in achieving business goals. Traditional security paradigms based on perimeter-driven firewalls do not scale for communication between workloads within the cluster and 3rd-party APIs outside the cluster.
Cloud Security Architecture: A Practical Guide
Cloud computing security architecture describes how an organization secures data, applications, and workloads hosted across cloud environments. It specifies all technologies — both software and hardware — allocated for protecting cloud assets, and defines the security responsibilities shared between the cloud services provider and the organization. Cloud security architecture is a component of the organization’s overall security approach.
Make Account Compromise a Non-Issue: Introducing Immutability for Microsoft Azure VMs
Author Brian Mislavsky Rubrik Storage Tiering for Microsoft Azure now leverages Azure Blob immutability by default. In our Winter Release, we introduced Storage Tiering for Microsoft Azure as a way for Rubrik customers to further protect workloads in Microsoft Azure by enabling the ability to logically air gap data between Azure Subscriptions as well as potentially decrease long term storage costs by almost 40%.
Bringing cloud native application security full circle
The cloud has enabled organizations to build and deploy applications faster than ever, but security has become more complex. The shift to cloud has created a world where everything is code — not just the applications, but also the infrastructure they run on. So, any security issue within an application or cloud environment can put an entire system at risk. And keeping that cloud native application stack secure is increasingly the responsibility of development teams.
Exceptions Should Not Become The Rule
It is a sentence I hear a lot; “We treat Microsoft 365 as an exception in our cloud security because it is a managed app.” You might think that’s a reasonable approach to take, after all Microsoft’s security credentials are impressive, all OneDrive app traffic is encrypted, and there are plenty of other unmanaged cloud applications in use as shadow IT all over your organisation that pull your attention.
How to Secure Amazon EC2 with Sysdig
Elastic Compute Cloud (EC2) is arguably one of the most popular AWS services, and really needs no introduction but here is one anyway. With Sysdig, you can secure EC2 by managing configuration and permissions risk, meeting compliance requirements, and managing vulnerabilities on containers and host VMs. When it comes to EC2 and Hosts themselves, Sysdig Secure alerts us in multiple ways.
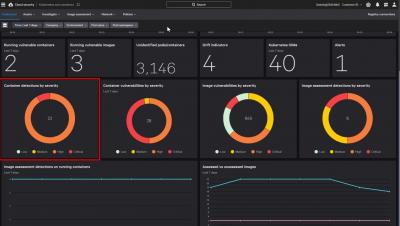
Code to cloud and back to code!
Pillars of Amazon Web Services: Security, Identity, and Compliance
As more and more businesses adopt cloud computing services for their operations, the threat against cloud infrastructure is also increasing. AWS, the huge cloud service provider in the market, provides many security features to secure the cloud structure and customer data. It is essential to understand the service provider’s security policy before adopting it for the business.