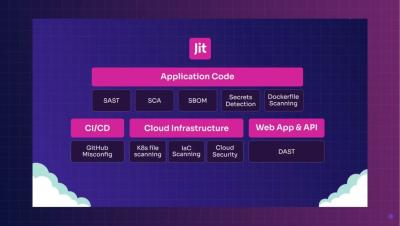
Essential Considerations When Choosing a DSPM Solution
The advent of cloud technology has revolutionized organizations’ data use and security practices. Cloud development has decentralized data management, with development and DevOps teams — and now business intelligence (BI) and AI teams — dispersing data across multiple cloud service providers, regions and applications. This decentralization has fueled the proliferation of shadow data and heightened the risk of unintentional data exposure.