Celebrating new milestones plus enterprise-ready features and more AI capabilities
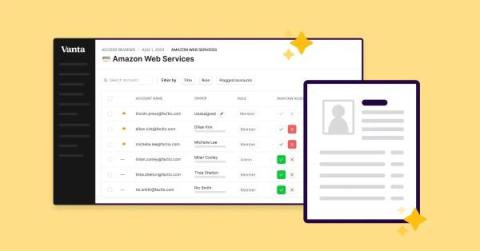
Today we’re excited to share several milestones as we continue on our mission to secure the internet and protect consumer data. And we’re just getting started. As we continue to reimagine GRC tools for the future of trust, we’ve built enterprise-ready features and rolled out additional Vanta AI capabilities along with support for the NIST AI Risk Management Framework.