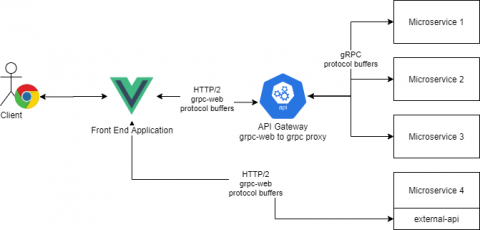
Kong Mesh and Styra DAS - securing modern cloud-native applications
Back at KubeCon North America 2017, many speakers declared that 2018 would be “The Year of the Service Mesh”. Just a year later, in the 2019 CNCF Survey1, it was reported that 18% of surveyed organizations were using a service mesh in production, and by 20202 (the most recent survey published at the time of this writing) that number rose to 27%.