AI-Assisted Attacks Are Coming to OT and Unmanaged Devices - the Time to Prepare Is Now
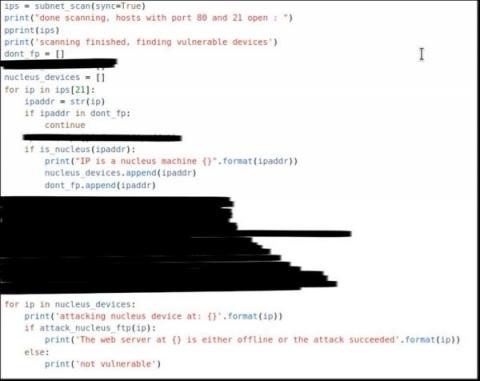
Malicious code is not difficult to find these days, even for OT, IoT and other embedded and unmanaged devices. Public exploit proofs-of-concept (PoCs) for IP camera vulnerabilities are routinely used by Chinese APTs, popular building automation devices are targeted by hacktivists and unpatched routers used for Russian espionage.