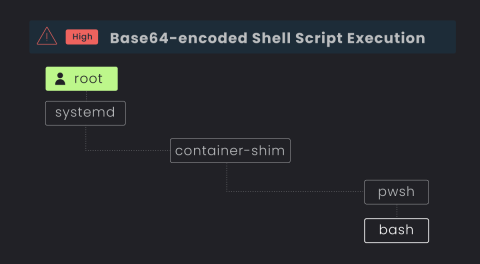
Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
7 Ways to Strike Balance Between Technical Debt and Security Posture in The World of Open Source
Why Traditional EDRs Fail at Server D&R in the Cloud
In the age of cloud computing, where more and more virtual hosts and servers are running some flavor of Linux distribution, attackers are continuously finding innovative ways to infiltrate cloud systems and exploit potential vulnerabilities. In fact, 91% of all malware infections were on Linux endpoints, according to a 2023 study by Elastic Security Labs.
The Ultimate Guide to IoT Gateways: Everything You Need to Know!
In the rapidly growing world of the Internet of Things (IoT), IoT gateways have emerged as essential components that bridge the gap between IoT devices and the cloud. As the backbone of IoT networks, these gateways not only streamline communication and data processing but also ensure the security of connected devices.
Introducing advanced session audit capabilities in Cloudflare One
The basis of Zero Trust is defining granular controls and authorization policies per application, user, and device. Having a system with a sufficient level of granularity to do this is crucial to meet both regulatory and security requirements.
Revolutionising the Road: The Impact and Advantages of IoT Automotive Innovations
A new era of innovation is upon us, revolutionizing the automotive industry with the power of the Internet of Things (IoT). This ground-breaking technology is transforming the way we manufacture, operate, and maintain our vehicles, leading to smarter, safer, and more efficient driving experiences. But what exactly does this mean for the future of transportation, and how can we harness the full potential of these emerging technologies?
Key learnings from the State of Cloud Security study
We recently released the State of Cloud Security study, where we analyzed the security posture of thousands of organizations using AWS, Azure, and Google Cloud. In particular, we found that: In this post, we provide key recommendations based on these findings, and we explain how you can leverage Datadog Cloud Security Management (CSM) to improve your security posture.
Nextcloud Review: Is Self-Hosting Your Cloud Storage Worth It?
Is Traditional EDR a Risk to Your Cloud Estate?
Organizations are transitioning into the cloud at warp speed, but cloud security tooling and training is lagging behind for the already stretched security teams. In an effort to bridge the gap from endpoint to cloud, teams are sometimes repurposing their traditional endpoint detection and response (EDR) and extended detection and response (“XDR) on their servers in a “good enough” approach.