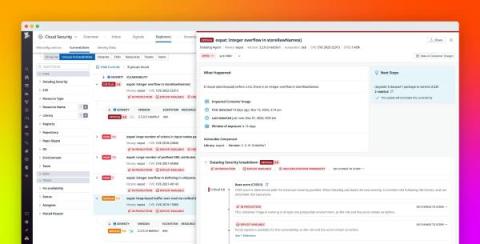
Cyber Week: Analyzing Internet traffic and e-commerce trends
Throughout the year, special events lead to changes in Internet traffic. We observed this with Thanksgiving in the US last week, where traffic dipped, and during periods like Black Friday (November 24, 2023) and Cyber Monday (November 27, 2023), where traffic spiked. But how significant are these Cyber Week days on the Internet? Is it a global phenomenon? Does e-commerce interest peak on Black Friday or Cyber Monday, and are attacks increasing during this time?