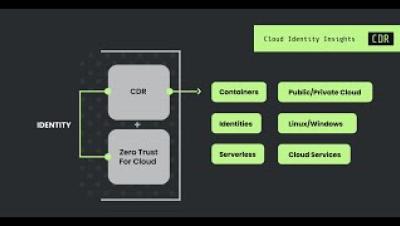
Strengthening Australia's Government Data and Digital Services with Splunk Digital Resilience
As the Splunk Industry Advisor to the Australian public sector, I work closely with government organisations and their leaders to understand their goals, objectives and the challenges they face in achieving digital resilience. This blog shares perspectives on how Splunk works with the Australian government to provide a unique approach to solve some of the public sector's toughest challenges.