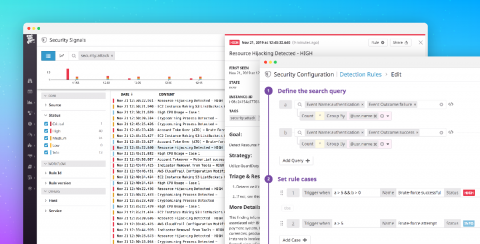
The Importance of Alert Grouping
Alerts are one of the most important information sources when it comes to cyber security. They notify and inform your IT team about ongoing cyber threats, security events and any other incident that might threaten your organization. In this article, we will focus on alert grouping and why it is important for the security of your organization.