Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Visibility, Vulnerabilities and VPNs - Extending Your Corporate Security Policies and Procedures to Cover Remote Workers
We’ve heard a lot about the drastic measures that organizations in North America and Western Europe are taking to protect their employees against the coronavirus. But as we all know, COVID-19 is a global pandemic. Organizations all over the world now find themselves in a position where they need to take action on their policies and procedures. Take the Middle East, for instance.
Virtual safety: How to teach your kids cybersecurity best practices
Confession: I am a security practitioner. I am also a mom. What I am not is a homeschool teacher. Earlier this year, I spoke to the 5th- and 6th-grade classes at my son’s Innovation Day about cybersecurity. I discussed what it means to be a cybersecurity practitioner and how the practice of cybersecurity affects everyday life.
Generating MITRE ATT&CK® signals in Elastic SIEM: Sysmon data
Many mature security teams look to the MITRE ATT&CK® matrix to help improve their understanding of attacker tactics, techniques, and procedures (TTPs) and to better understand their own capabilities relative to these common adversarial approaches. With the release of Elastic Security 7.6, Elastic SIEM saw 92 detection rules for threat hunting and security analytics aligned to ATT&CK.
How to Conduct a Vulnerability Assessment
A considerable portion of cyber-attacks target simple and unnoticed security vulnerabilities, that is why conducting a thorough vulnerability assessment is vital for each and every organization. Read our article to learn more. As the technology advances, a vast majority of the business processes are realized online. Each and every day we share important files, send e-mails, conduct communication with our team and customers, and we do all these tasks online.
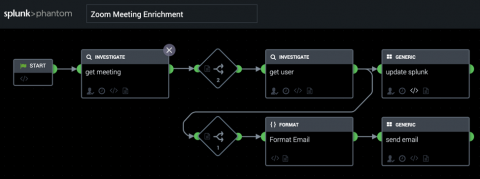
Zoom in on Security in a Remote Work World
Our world has been turned upside down by COVID-19. Whether it's strategically planning our grocery run decontamination process, or trying to keep the kids quiet for even one single moment while on a conference call — things are different. One very evident difference is the change in the way we meet with each other. And one technology enabling this change is Zoom.
Can incident response be fun?
Cyber attacks are unfortunately inevitable. It’s important to security harden your networks as much as possible. But your organization must also be prepared for incident response. Effective incident response involves an awareness of various cyber risks and threats, having a plan to respond to the various ways they manifest, and having a team that can think quick on their feet when they actually occur.
Slack phishing attacks using webhooks
Slack is a cloud-based messaging platform that is commonly used in workplace communications. It is feature-rich, offering additional functionality such as video calling and screen sharing in addition to a marketplace containing thousands of third-party applications and add-ons. Slack Incoming Webhooks allow you to post messages from your applications to Slack.
5 key network aspects to focus on for HIPAA compliance
The Health Insurance Portability and Accountability Act, also known as HIPAA, is a compliance standard that was implemented after all health-related information was digitized. The crux of the act is to ensure that all sensitive electronic protected health information (ePHI) has restricted, secure access. Various aspects of your network determine your compliance with HIPAA standards. Let’s discuss some of these important components in detail.
BitSight vs Prevalent Comparison
The unfortunate truth is outsourcing to third-parties introduces significant cyber risk. The news is inundated with third-party data breaches and data leaks. With the average cost of a data breach at nearly $4 million globally, it makes sense to invest in tools to prevent data breaches. This is why cybersecurity vendor risk management (VRM) has become a top priority for CISOs and other members of senior management, even at the Board level.