Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Audit
ADAudit Plus User Logon Reports, Part 5: Detect users' last logon times on workstations
ManageEngine ADAudit Plus is a UBA-driven auditor that bolsters your Active Active (AD) security infrastructure. With over 250 built-in reports, it provides you with granular insights into what’s happening within your AD environment, such as all the changes made to objects and their attributes. This can include changes to users, computers, groups, network shares, and more.
What Is an Audit of Internal Control Over Financial Reporting?
Startups! Here's Your Guide to SOC 2: Audit Preparation
As a startup, it can be challenging to navigate the complex world of compliance. From financial regulations to data privacy laws, there are many different rules and regulations that a new business must adhere to. However, achieving good compliance is essential for the long-term success of any startup. A well-designed compliance program can not only help a startup avoid legal and reputational risks, but it can also improve overall efficiency, productivity, and business growth.
Why does your SaaS application need audit logs?
Audit logs are an important tool for keeping track of activity within your SaaS application. These logs provide a detailed record of the actions taken by users and can be used to monitor for potential security breaches, compliance violations, and other issues. Let’s explore some of the key reasons why you need audit logs for your SaaS app.
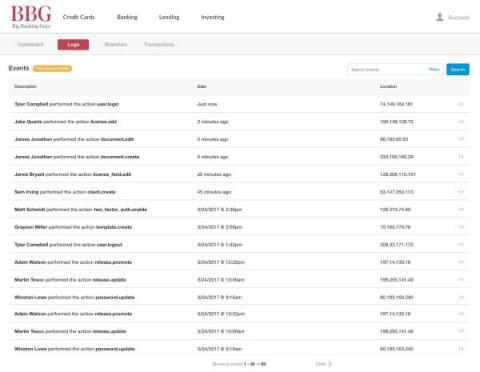
Audit your users' logons: ADAudit Plus User Logon report
ManageEngine ADAudit Plus is a UBA-driven auditor that fortifies your Active Directory (AD) security infrastructure. With over 250 built-in reports, it provides you with granular insights into what’s happening within your AD, such as all changes made to objects and their attributes. This can include changes to users, computers, groups, network shares, and more.
Audit: Force audit policy subcategory settings
What to Do If You're Unprepared for a SOC Audit
The System and Organization Controls, or SOC (sometimes referred to as service organizations controls), are the required security control procedures set as non-mandatory, internationally-recognized standards that help businesses measure how SaaS companies and service organizations manage data and sensitive information. Organizations or businesses that have successfully passed the SOC auditing process can attest to the quality of their security controls for regulating customer data.
The top three differences between an open source audit and an open source scan
How long does a SOC 2 audit take?
The length of an average SOC 2 audit depends on a lot of variables, but with Vanta, customers can get a SOC 2 Type I report in weeks, and a SOC 2 Type II report within months. Audit timelines are difficult to project because each organization has different capabilities, resources, and goals. But after helping thousands of businesses tackle SOC 2 audits, we’ve developed a reliable timeline of what most customers can expect.