Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
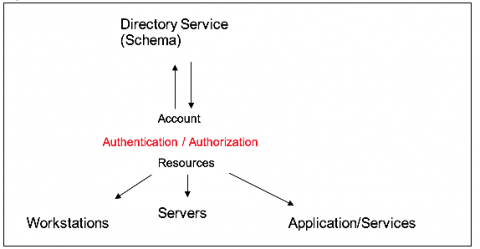
Cyber Security for Industrial Control Systems
It is no secret that humans make mistakes. In order to reduce the damages and harms caused by human error, cyber security is a must for industrial control systems. Keep reading to learn more. Unfortunately, humans make mistakes. There are many reasons behind this fact, such as the limited capacity of our working memory or our short attention span. Regardless of our experience, no matter how well trained we are, we all make mistakes, and it is okay. Mostly.
Detecting, Reporting and Mitigating Vulnerabilities for Go Modules
Go Module vulnerabilities frustrate the lives of many Go developers and can turn a simple project into a battle of endurance between the dev and their patience. With the process of CI/CD shifting left more and more, it’s becoming even more pertinent for developers to be able to track and report vulnerabilities as early as possible. JFrog GoCenter can help track and mitigate vulnerabilities and make the lives of Go developers easier.
The importance and security concerns of staying connected during the COVID-19 pandemic
Unsplash The COVID-19 pandemic sweeping the globe has effectively put a stop to the bulk of face-to-face interactions. With social distancing and shelter in place orders in effect, people are stuck at home and relying on the Internet as not only a tool for communication and entertainment but as their only way to earn money during this hectic and uncertain time.
Targeted Ransomware Attacks in Taiwan
Following reports of suspected ransomware attacks against various organizations in Taiwan, this report summarizes what is known of the threats thus far as well as providing recommendations for those that either operate in the targeted industries or region.
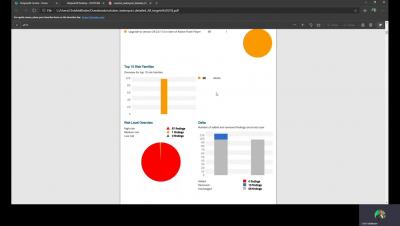
Gartner 2020 Magic Quadrant for Application Security Testing: Key Takeaways
The Gartner Magic Quadrant for Application Security Testing 2020 reports a 50% increase in the number of their end-user client conversations about DevSecOps and AST (Application Security Testing) tools, in 2019. According to the report, users continue to adopt DevOps methods like integrating security into the software development lifecycle from the earliest stages of development.
How implementing a BYOD initiative helps prepare remote workers for COVID-19 era challenges
As the COVID-19 pandemic continues to force employees to work from home, businesses are facing new and unique challenges to ensure business continuity. When remote work is mandated due to COVID-19, the transition isn’t smooth for many businesses; not every business has the infrastructure to make the abrupt shift, even given the immediate need to go remote.
Email, security, and breaches
Email-based attacks can take many forms, and are typically deployed by cybercriminals in order to extort ransom or leak sensitive data. Just recently, a banking Trojan named Trickbot targeted Italy, a hotspot for COVID-19 cases, with email spam campaigns. While the email subject line is in line with the daily concerns and talks about spread of the virus, the attachment was actually a malicious script.
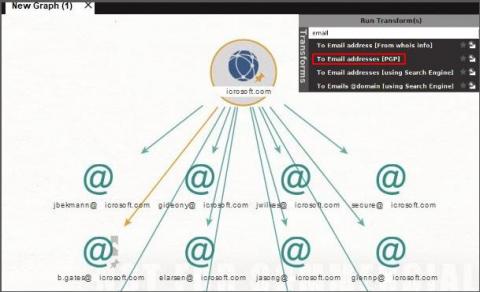
Profiling "VIP Accounts" Part 1
What is Continuous Security Monitoring?
Continuous security monitoring (CSM) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support organizational risk management decisions. Organizations need real-time visibility of indicators of compromise, security misconfiguration, and vulnerabilities in their infrastructure and networks.