Domain controller patch alert! Vulnerability grants domain admin access in 10 seconds
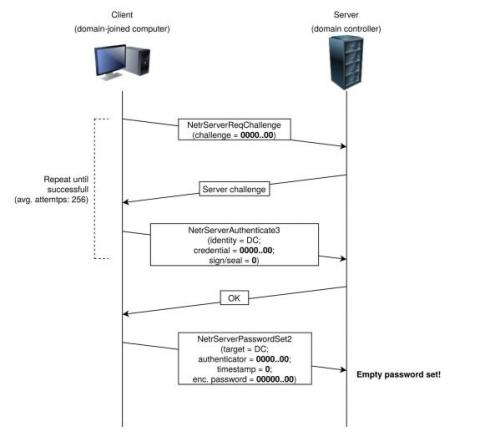
A critical Active Directory vulnerability (CVE-2020-1472) has been making headlines for being the most notorious elevation of privilege bug because it can affect all computers and domain controllers in an organization. This high-risk vulnerability, dubbed Zerologon, gives threat actors easy, instant access to domain controllers without requiring any additional privileges. This attack does not even require a user to be authenticated; the user just needs to be connected to the internal network.