Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Search
What is the best paid search intelligence tools
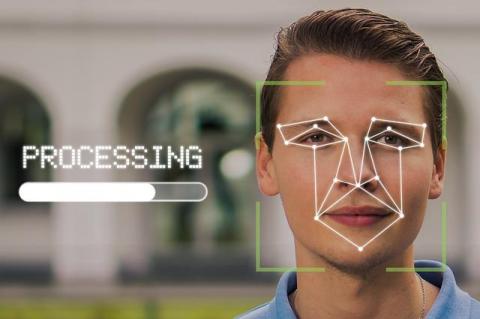
How to Use Facial Recognition for Face Search
Searching data in Devo
Finding Results Faster With Egnyte's Search Enhancements
According to the latest estimates around 328 million terabytes of new data is generated daily. Given this massive volume of information, the usability of a search engine to effectively provide relevant search results is crucial for the growth of any organization.
SOLR vs. Elasticsearch: What's the best search engine for 2022?
While modern businesses depend on data to stay ahead of the competition, data alone isn’t enough. They also need efficient search engines to quickly index and search through millions of records to make sense of the data. Today we’re looking into SOLR and Elasticsearch, the two heavyweights in this domain, to compare their performance differences and use cases.
Get the Most Out of the Desktop App with Search, Recents
Egnyte users want to get the files they need as fast as possible. Less time spent scouring folders means more time doing the work that really matters, and one of the best ways to do that is with the Egnyte Desktop App. With the Egnyte Desktop App you get real-time access to all your files and folders stored in the cloud, directly from your computer.
Run a search with selected columns only
Table of Contents:
00:00 - Introduction
00:49 - Using Finders - Learn more on https://bit.ly/3tXaCTD
01:31 - Using Free Text Query - Learn more on https://bit.ly/3jQpcaS
02:02 - Modify column selection
02:45 - Unrevealed columns (Extra) - Learn more on https://bit.ly/2OI6abb
5 Common Elasticsearch Mistakes That Lead to Data Breaches
Avon and Family Tree aren’t companies you would normally associate with cybersecurity, but this year, all three were on the wrong side of it when they suffered massive data breaches. At Avon 19 million records were leaked, and Family Tree had 25GB of data compromised. What do they have in common? All of them were using Elasticsearch databases. These are just the latest in a string of high profile breaches that have made Elasticsearch notorious in cybersecurity.
Elasticsearch Vulnerability: How to Remediate the most recent Issues
An Elastic Security Advisory (ESA) is a notice from Elastic to its users of a new Elasticsearch vulnerability. The vendor assigns both a CVE and an ESA identifier to each advisory along with a summary and remediation details. When Elastic receives an issue, they evaluate it and, if the vendor decides it is a vulnerability, work to fix it before releasing a remediation in a timeframe that matches the severity.