Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SecOps
Top Cyber Attacks of May 2022
Torq Product Updates for June 2022: Transformation is the Key
Right now, much of the security world is focused on the RSA conference in San Francisco, California. The Torq team has been preparing for the event for months—and we’re thrilled that we finally get a chance to talk about Torq in person with other security professionals.
4 Database Access-Control Methods to Automate
Niall Heffernan: How to empower your security operations team to focus on higher value strategic work
In our sixth episode of the Future of Security Operations podcast, Thomas speaks with Niall Heffernan, Head of Security at Cygnvs, a former Senior Manager of Information Security at Informatica, and a Lecturer for BSc, HDIP, PGDip, and MSc students studying in the Cybersecurity courses at the National College of Ireland.
CVE-2022-26134 - Critical Vulnerability in Confluence Server & Data Center
Three reasons why Security Operations Centers (SOCs) are adopted
Company IT and security teams are facing cybersecurity challenges that increasingly test their defensive capabilities. Organizations have to protect themselves from a growing number of incidents (one attack every 39 seconds, according to the University of Maryland) and sophisticated threats, many of which have serious consequences.
Brute-Force Attacks: How to Defend Against Them
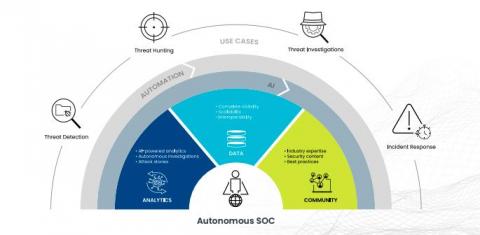
Emerging Technologies and Evolving Analysts Are Giving Rise to the Autonomous SOC
Fueled by the need to detect new, emerging threats while supplying meaningful feedback upstream to anticipate and prevent future ones, the modern SOC is the engine that protects organizations worldwide. The heart of that engine is common to all SOCs since they debuted more than a decade ago: people.