Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SecOps
How Chatbot Automation Benefits Security Teams
When you hear the term “chatbot,” your mind may at first turn to things like robotic customer support services on retail websites – a relatively mundane use case for chatbots, and one that is probably hard to get excited about if you’re a security engineer. But, the fact is that chatbots can do much more than provide customer support.
Incident Response: Compare Options for Your Organization
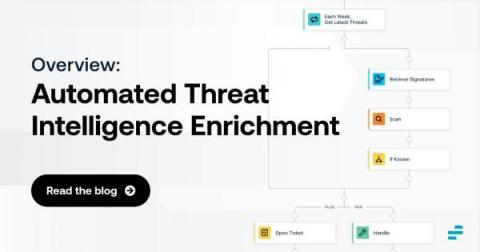
Automated Threat Intelligence Enrichment: An Overview
Discovering security threats is good and well. But, in many cases, simply knowing that a threat may exist is not enough. Instead, you also need threat intelligence enrichment. Threat enrichment plays a critical role in helping to evaluate and contextualize threats, root out false positives and gain the insights necessary to mitigate risks as efficiently and quickly as possible.
Reflections on AWS re:Inforce 2022
CVE-2022-22280 - Critical SonicWall Vulnerability Impacting Analytics On-Prem and Global Management System Products
Cisco Nexus Dashboard Vulnerabilities: CVE-2022-20857, CVE-2022-20858 and CVE-2022-20861
CVE-2022-26136 & CVE-2022-26137 - Multiple Critical Vulnerabilities in Atlassian Products
Are You Missing These Benefits of a 24/7 SOC?
When it comes to protecting your business, there is no such thing as being too cautious. In today's increasingly connected world, cyberattacks are becoming more and more common, and the stakes are higher than ever before. That's why many businesses are turning to 24/7 SOC through a managed security services provider (MSSP) to protect their business.
How To Put Cloud Nimble to Work to Shift Left Security
Shifting security left means preventing developers from using unacceptably vulnerable software supply chain components as early as possible: before their first build. By helping assure that no build is ever created using packages with known vulnerabilities, this saves substantial remediation costs in advance. Some JFrog customers restrict the use of open source software (OSS) packages to only those that have been screened and approved by their security team.