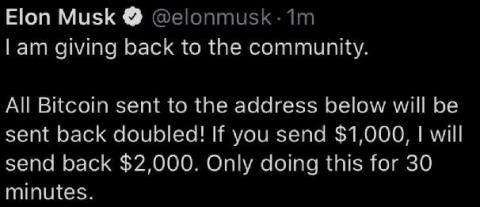
Unfolding the Twitter security incident
In case 2020 wasn’t dystopian enough, here’s some more unbelievable news. On July 15, 2020, social media giant Twitter admitted it fell victim to a security breach. The attackers targetted 130 Twitter accounts, including several belonging to high-profile individuals such as elected officials; former president Barack Obama; and business leaders including Bill Gates, Jeff Bezos, and Elon Musk.