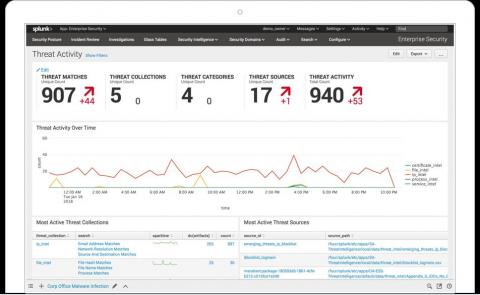
Introducing a New Splunk Add-On for OT Security
The lines Between IT and OT are blurring. With IT and Operational Technology (OT) systems converging, ensuring the security of devices, applications, physical locations and networks has never been more difficult or more important. There is a growing recognition by security professionals that they have a readiness and visibility problem in plain sight.