Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Attacker Floods npm With Crypto-Mining Packages that Mine Monero When Installed with Default Configuration
Monero (XMR) is an open-source, privacy-oriented cryptocurrency that was launched in 2014. It uses a public distributed ledger containing technology that obscures transaction details to ensure the anonymity of its users. Monero maintains egalitarian mining, allowing anyone to participate. As tempting as it may seem, some go a step further and use the infrastructure of others to participate in mining. Cryptocurrency mining was originally performed using CPUs, and Monero was no different.]
Q&A with: Rami Sass, CEO and co-founder of Mend (formerly WhiteSource)
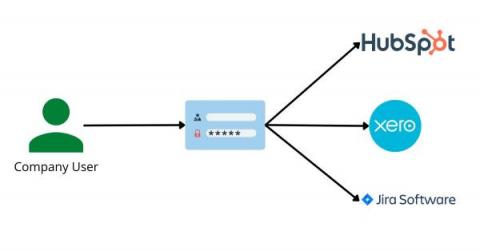
Understanding SAML SSO, the basics from the user side
I have always worked in tech, so have always needed to understand the technical nature of the products we are building. This process has always been over-complicated for me so I now always try to write a guide for non-technical people like me. It turns out that once you understand it you can explain it to other non-technical people much easier! So here we go as I try to explain SAML (Security Assertion Markup Language) SSO (single sign-on) and why BoxyHQ makes it so easy to implement.
Understanding SAML SSO, the basics from the solution provider's side
This article follows my first article in which I explain the basics of SAML from the users' side. If you haven't read that one already I would recommend reading that one first here. In this article, we are going to take a look at what SAML authentication and setup look like from the solution providers' perspective. If you are a B2B solutions provider and you plan to have enterprise customers they will likely ask that your product supports SAML SSO.
Choosing an RDP Client
Controlling your Windows PC remotely can open a world of possibilities; remote work, remote assistance, remote system diagnosis and network troubleshooting are just some of the advantages of using Remote Desktop Protocol or RDP. Developed by Microsoft, RDP allows you to remotely connect to another computer over a network, giving you full access to and control over the computer’s software, data and resources.
rusted SBOMs delivered with the JFrog Platform and Azure
A day In The life of a Fashion Products Company CISO - Vikas Yadav
Snyk supports strong EMEA growth with regional data residency
Building a secure CI/CD pipeline with GitHub Actions
GitHub Actions has made it easier than ever to build a secure continuous integration and continuous delivery (CI/CD) pipeline for your GitHub projects. By integrating your CI/CD pipeline and GitHub repository, GitHub Actions allows you to automate your build, test, and deployment pipeline. You can create workflows that build and test every pull request to your repository or deploy merged pull requests to production.