Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
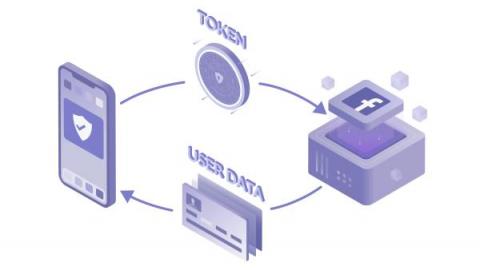
How OAuth 2.0 Works
The modern human likely has profiles on dozens of applications. Whether it’s social media applications, music/video streaming, or workspace resources, each of us must manage accounts that contain personal information. Over time, these siloed applications have become increasingly connected. Twitter allows news sites to directly tweet, Discord searches Facebook for suggested friends, and Jira creates user accounts using Github profiles.
Why you need a Kubernetes admission controller
Unless you have experience as a Kubernetes operator or administrator, admission controllers may be a new feature for you. These controllers work mostly in the background and many are available as compiled-in plugins, but they can powerfully contribute to a deployment’s security. Admission controllers intercept API requests before they pass to the API server and can prohibit or modify them.
What is Policy Based Access Management?
We’re excited to be included in the first Policy Based Access Management (PBAM) market report! The KuppingerCole Analysts AG’s 2022 Market Compass provides an excellent overview of how the access market is transforming and emerging vendors in the space.
Generating fake security data with Python and faker-security
Snyk recently open sourced our faker-security Python package to help anyone working with security data. In this blog post, we’ll briefly go over what this Python package is and how to use it. But first, we’ll get some context for how the factory_boy Python package can be used in combination with faker-security to improve your test-writing experience during development. Note: Some knowledge of Python is helpful for getting the most out of this post.
Cybernews/ WhiteSource: It's No Longer a Matter of 'If', but 'When' an Organization Will Be Targeted by Threat Actors
From ransomware and viruses to data breaches, there are many types of security threats to look out for. Because they’re becoming more complex, it’s getting more difficult to secure your organization and avoid the financial and reputational consequences. While some organizations use traditional security measures, such as encrypting data or using antivirus software, businesses should also take a look at more advanced solutions, such as open source security and license management services.
Securing CI/CD with Rob Zuber
Practical Tips for Organizing Kubernetes RBAC
Kubernetes supports several authorization methods, but the best-known and one of the most versatile is RBAC. Role-based access control implements a mechanism for restricting and controlling user access to resources of a system by using roles attached to users.
User Office Hours: Exploring Snyk Container
The ultimate guide to Python pickle
During application development, we often need to persist complex data (like objects) for use in different runtimes. However, maintaining persistence within complex data structures and objects is far from straightforward. In Python, you can use the built-in pickle library to handle this process. Pickle can serialize a Python object into a flat byte stream (pickling) as well as transform a byte stream back into a Python object (unpickling).