Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Enabling Self-Service Recovery in a Multi-Tenant Kubernetes Environment with CloudCasa and Capsule
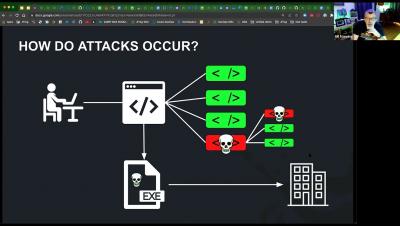
How Malicious NPM Packages Make Your Apps Vulnerable
Introducing Mend Supply Chain Defender Integration with JFrog Artifactory
When it comes to understanding the difference between open source software vulnerabilities and malicious threats, it’s helpful to think in terms of passive vs. active threats. Vulnerabilities can be attacked and exploited, but in a vacuum don’t pose a threat. Malicious threats are different —– they involve a threat actor actively planning to attack you.
Amazon RDS Just-in-Time (JIT) Access With Teleport and Slack
This blog is part three in a series about secure access to Amazon RDS. In Part 1, we covered how to use OSS Teleport as an identity-aware access proxy to access Amazon RDS instances running in private subnets. Part 2 explained implementing single sign-on (SSO) for Amazon RDS access using Okta and Teleport. In Part 3, we will guide you through the steps to configure privilege escalation for just-in-time access requests for Amazon RDS access.
Software Supply Chain Security for Open Source Projects
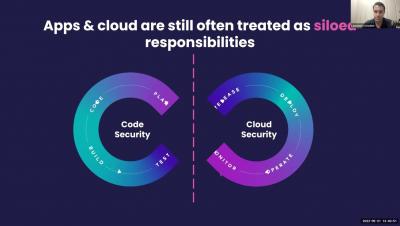
Code to cloud and back to code!
Developing Secure Software With Confidence
Software development and security often have separate challenges and concerns. Developers are worried about pushing software to production in a timely manner. Security teams worry about the security of the code being pushed. Veracode offers a solution that meets the needs of both sides. On Peerspot, where Veracode is ranked number one in application security, users discuss how Veracode enables them to build an advanced application security program.