Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Scaling Developer Security in Financial Organisations: Best Practices from ClearBank
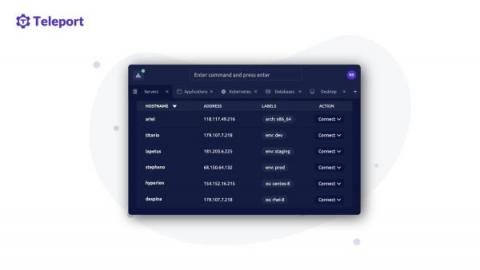
Kubernetes Access support for Teleport Connect
Teleport 10.3 was released on September 30, 2022 along with a lot of new features, bug fixes and improvements. This blog post will focus on one new feature that deserves a deeper dive.
Cybercriminals targeted users of packages with a total of 1.5 billion weekly downloads on npm
Another week, another supply chain incident. It’s been only nine days since the Mend research team detected the dYdX incident, and today we have detected another supply chain malicious campaign. On October 02, 2022 at 12:12 UTC, a new npm account was registered, and a package called nuiversalify was immediately uploaded. The same threat actor then proceeded to publish more typo/spellcheck squattings of popular packages until 14:03:29 UTC, with small but irregular time gaps between uploads.
This Week in VulnDB
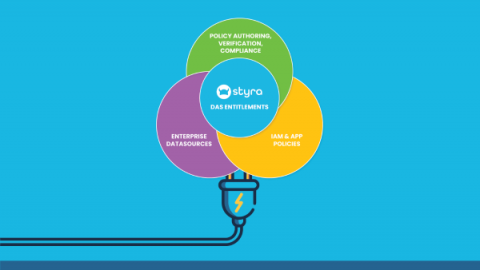
How Styra DAS Entitlements Power Application Authorization
With the power of modern cloud computing, enterprises are building and updating applications quicker than ever. Expanding your business through the cloud is a fast-paced endeavor, which can be daunting to IAM teams more familiar with on-premises setups. While running applications on self-hosted infrastructure is still a best practice in some cases, businesses are finding it easier than ever to find and pounce on opportunities for growth by shifting to the cloud.
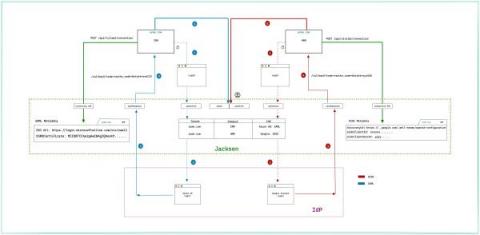
SSO Building blocks - SAML, OAuth 2.0 and OpenID Connect
We have already covered SAML at a high level from both user and application provider points of view. In this post, we'll dive into the technicalities of SAML, OAuth 2.0 and OpenID Connect and how these come together to serve as building blocks for Jackson SSO.