Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
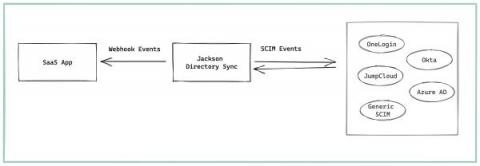
Understanding SCIM and Directory Sync
This article will walk you through everything you should know about SCIM and Directory Sync.
Sign your Git commits with 1Password
So 1Password CEO Jeff Shiner just committed code to one of my GitHub repositories. That’s strange. While he’s a developer at heart, I don’t think he gets much time to code these days. What’s going on here?
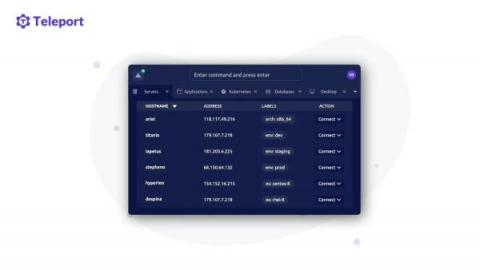
Teleport 10.2 - Teleport Connect for Windows and Directory Sharing
Teleport 10.2 was released on September 6th along with a lot of new features, bug fixes and improvements. This blog post will focus on two new features that deserve a deeper dive.
Cookie for a Thought - How to Manage HTTP Sessions
Whether it's password or passwordless authentication, multi-factor authentication, or any of the other identity verification shenanigans, in the end, our identity is deduced to a single session cookie! We can't deny the security importance of session cookies in web application access control.
Free and Protect Kubernetes Data with CloudCasa and Ondat
The adoption of Kubernetes and its ecosystem has continued its rapid growth, with over 5.1 million developers worldwide now using Kubernetes. Developers are adopting and utilizing Kubernetes to manage containerized workloads and services. Kubernetes has many benefits for organizations and developers including auto scaling, automated deployment and rollback, self-healing, loading balancing and application centricity.
CVE-2022-36085, OPA and Styra DAS
Testing the relatively new function mocking feature of OPA revealed a vulnerability in the Go API, where the use of the WithUnsafeBuiltins function on the compiler object — a deprecated legacy function used to declare a set of function names as unsafe, and as such rejected in the policy compilation stage — could be bypassed by mocking a function, effectively replacing it with one of the functions deemed unsafe.