Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Everything You Need to Know About CI/CD and Security
CI/CD is a recommended technique for DevOps teams and a best practice in agile methodology. CI/CD is a method for consistently delivering apps to clients by automating the app development phases. Continuous integration, continuous delivery, and continuous deployment are the key concepts. CI/CD adds continuous automation and monitoring throughout the whole application lifetime, from the integration and testing phases to delivery and deployment.
#DevOpsSpeakeasy at #KubeCon EU 2022 with James Strong on Supply Chain Security
Building Modern Access-Control for Cloud Applications with Or Weis | SnykLIVE Recording
BlackHat 2022 key takeaways - Everything you need to know from BlackHat 25
Securing Cloud Infrastructure with Teleport and AWS Identity Federation
Over the last decade, enterprises have accelerated the adoption of the cloud. According to the State of the Cloud report by Flexera, the average annual spend on cloud computing is over $62 million. As enterprises continue to invest in the cloud, AWS, the market leader in cloud computing, is growing at a rapid pace. The rise of cloud computing poses new challenges to enterprise IT. With each department migrating and managing their workloads in AWS, there is a proliferation of accounts, users and roles.
PyPi Malware Stealing Discord and Roblox Payment Info
Stranger Danger: Your Java Attack Surface Just Got Bigger
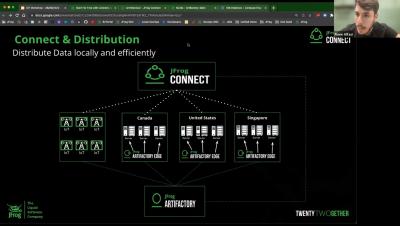
A new generation of OTA updates for Linux devices with Jfrog Connect
Why You Should Get Started with the Rego Policy Language
The Rego policy language is the backbone of Open Policy Agent (OPA), the policy enforcement tool that helps simplify cloud-native development at scale. With OPA Rego policy, the result is a reduced manual authorization burden, improved accuracy, and quicker time to market. But yes, there’s a learning curve, which makes Rego a main barrier to using OPA. You might be hesitant about the time investment needed to learn a new, highly specified language.