Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
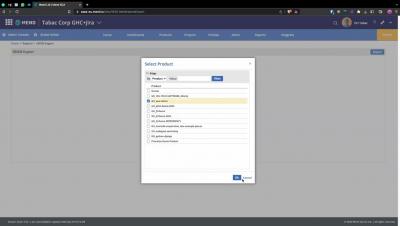
How to Create a CycloneDX SBOM Using Mend
4 things to identify and fix in your GPOs
Group Policy Objects (GPOs) act as a security layer in your infrastructure. They enforce rules, regulate permissions, and affect policies across the network. Do you want to assign additional privileges to certain groups? Delete a security group? Modify password policies across the network? Prevent software installations on critical systems? All of these and more can be accomplished using GPOs.
How to integrate Calico Image Scanner with Argo CI/CD
In today’s fast-paced software development environment, developers often use common public libraries and modules to quickly build applications. However, this presents a significant challenge for DevOps teams who must ensure that these applications are safe to use.
How to Handle Secrets in Terraform
DevOps engineers must handle secrets with care. In this series, we summarize best practices for leveraging secrets with your everyday tools.
Software Composition Analysis Explained
Open source code is everywhere, and it needs to be managed to mitigate security risks. Developers are tasked with creating engaging and reliable applications faster than ever. To achieve this, they rely heavily on open source code to quickly add functionality to their proprietary software. With open source code making up an estimated 60-80% of proprietary applications’ code bases, managing it has become critical to reducing an organization’s security risk.
Kubescape & Jit
Set Up Teleport Open Source in 5 Minutes | Step-by-Step
Build Enterprise Software with No-Code Thanks to Bubble.io
Building your enterprise applications on Bubble is now easier than ever with BoxyHQ, a single API to connect to enterprise Single Sign-On (SSO), and multiple security compliance features.
Explore the New Teleport 13 Features!
Once again it’s time for everyone’s favorite announcement: a brand new Teleport release! This release marks version 13 of Teleport and is packed with features, including a UI makeover. Let’s dive in!