Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Mend.io Collaborates with Kondukto's New Demo Hub
When you’re trying to choose the right application security solution, navigating the options on the market can be bewildering. At Mend.io, we know that software developers and DevOps professionals use multiple tools to identify security issues in different stages of the software delivery life cycle and different code types. And we’re dedicated to making every aspect of AppSec as seamless as possible, which includes making your solution selection as easy as it can be.
Integrations 101
Are you worried about the security of your software supply chain?
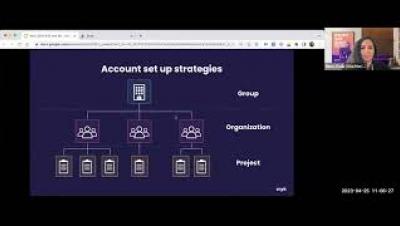
Best Practices for Your First 30 Days, April 2023
Root Cause Analysis for Deployment Failures
Root Cause Analysis (RCA) is a technique used to identify the underlying reasons for a problem, with the aim of trying to prevent it from recurring in the future. It is often used in change management processes to help identify the source of any issues that arise following any modifications to a system or process. RCA is something Tripwire Enterprise is often deeply tied into too.
Why is Cybersecurity Now a Global Governmental Concern?
Governments everywhere are increasingly concerned about implementing frameworks to improve the protection of personal and commercial information and defend national security against cyberattacks. I was recently in Australia, and it was hard to ignore the news that the Australian government released a discussion paper to shape its work on its 2023 – 2030 cybersecurity strategy.
Hackers Backdoor to Microsoft SQL Servers using Trigona ransomware
5 best practices for imaging hard drives
Accelerating Secure Infrastructure Automation with Red Hat Ansible Automation Platform and Styra DAS
I’m excited to announce the launch of Styra Declarative Authorization Service (DAS) and Open Policy Agent (OPA) as a Red Hat Ansible Certified Content Collection. Teams can now automate infrastructure deployments with the right guardrails in place to enable security-enhanced operations and align with regulatory compliance.