Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Compliance
ISO 27001 Compliance: What You Need to Know for Your Certification
Looking to become certified to the ISO 27001 standard? In this article you will learn what ISO 27001 is, the key terms and definitions, information security risks you need to consider, and the process for meeting your compliance and certification requirements.
Titania Launches New Module for Organizations Working with U.S. Government Agencies to Meet Cybersecurity Compliance Accurately
CMMC 2.0 Overview: What Changed?
The Cybersecurity Maturity Model Certification (CMMC) is an emerging program created to ensure cyber protection of vulnerable Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) for companies within the Defense Industrial Base (DIB).
LimaCharlie Achieves SOC 2 Certification
LimaCharlie has successfully completed its Service Organization and Control (SOC 2) audit. The audit was conducted by the Johanson Group, a leading professional service firm that focuses on SOC 2 & 3 examinations for public and private companies. The Johanson Group counts Cisco, Symantec and Broadcom among their many clients. They have members on the team that are Certified Information System Auditors (CISA) and are Certified Information Systems Security Personnel (CISSP).
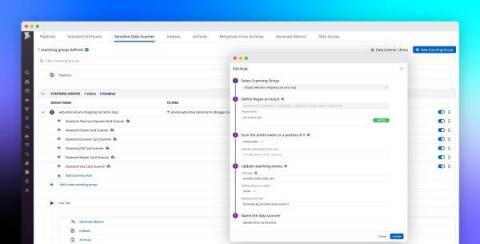
Build a modern data compliance strategy with Datadog's Sensitive Data Scanner
Within distributed applications, data moves across many loosely connected endpoints, microservices, and teams, making it difficult to know when services are storing—or inadvertently leaking—sensitive data. This is especially true for governance, risk management, and compliance (GRC) or other security teams working for enterprises in highly regulated industries, such as healthcare, banking, insurance, and financial services.
Selecting the right cybersecurity framework for your organization
Who needs CMMC certification (Resource Guide for 2022)
If your company works with the US Department of Defense (DoD) as a contractor or subcontractor, you will need to prepare to meet CMMC requirements in order to successfully bid on and win contracts. This recent development has been a significant adjustment for small organisations who wish to work with or continue working with the DoD.
What is Compliance Management and Why Is It Important?
Every business has a set of rules and regulations that it must uphold. To maintain compliance, businesses must adhere to the regulations and laws specific to their industry. The problem is, these regulations are constantly changing, and failure to stay up-to-date can lead to serious financial strains and damage to company reputation. Let’s explore how effective compliance management can ensure the continuity and security of your organization.
What Types of Security Capabilities Do Managed Service Providers (MSP) Offer?
Last time, I discussed the four basic types of managed service providers (MSPs) with which organizations commonly partner. Those categories help to determine the types of services offered by MSPs. In general, MSPs provide five primary services to customers.