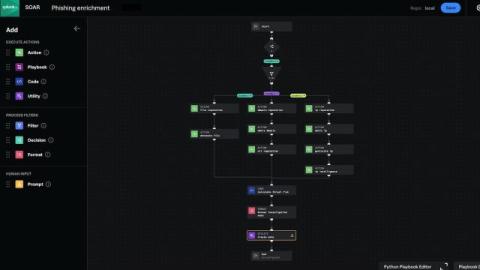
Once and future code snippets: How AI reignites risk
Code snippets copied from copyleft-licensed open source projects represented the biggest risk in software 15 years ago. The Heartbleed vulnerability, discovered in April 2014, brought to the fore concerns about the security of open source components, and license risk took a bit of a back seat. But the problem never went away. Now, the advent of Generative AI as a tool for writing software is shining a new light on the issue.