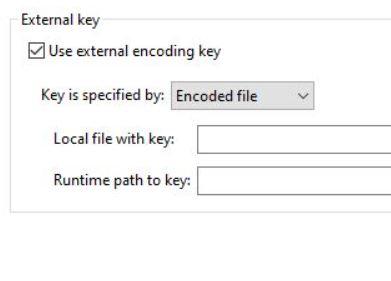
3 Critical Lessons from 2020's Largest GitHub Leaks
2020 has been a very challenging year for teams and organizations across the world. This has been especially true for security teams, who’ve been responsible for managing the technological risks associated with their organization’s response to the pandemic. With security teams focused on mitigating the seismic impacts that the pandemic has had on their organization’s infrastructure, some of the security problems that emerged before the pandemic have been overlooked.