Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Data Loss vs. Data Leaks: What's the Difference?
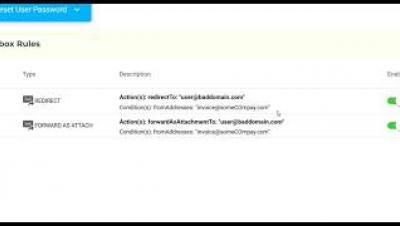
Data loss refers to the unwanted removal of sensitive information either due to an information system error, or theft by cybercriminals. Data leaks are unauthorized exposures of sensitive information through vulnerabilities on the digital landscape. Data leaks are more complex to detect and remediate, they usually occur at the interface of critical systems, both internally and throughout the vendor network.
U.S. Critical Infrastructure: Addressing Cyber Threats and the Importance of Prevention
The critical infrastructure of the United States includes all those systems and assets that are essential to the proper functioning, economy, health, and safety of American society.
Top 3 NLP Use Cases for ITSM
How can eCommerce portals make shopping secure?
ECommerce security protects your company and customer data from cyber-attacks and malicious bots. As an eCommerce business owner, you must ensure that all data is handled securely to avoid a breach. Poor eCommerce security can have many negative impacts on a business. Customer trust relies on great customer experience, and when customers enter their personal details into your website, they expect it to be protected.
Remediate Office 365 Risks in App
An Introduction To Cloud Security Posture Management (CSPM)
Many organizations are equipped to handle insider threat and external, common well-known challenges (like malware, for instance). These so-called “intentional” threats can be addressed through proactive security measures and best practices. But what about the unintentional risks that come with operating in a cloud-first environment? Unintentional mistakes, such as misconfiguring cloud infrastructure, can be equally devastating.
Asymmetrical threats in Cybersecurity
Security and defense theory are inextricably entwined. Consider medieval castles. They were designed as a defensive mechanism that provided security to those within, most of whom were simply civilians hiding behind the walls for protection from invaders. Within cybersecurity, multiple concepts from defense and war theory can be applied to better address the cyber risks facing organizations. In fact, the term Bastion Host refers to a Bastion which has very militaristic connotations.
Complete Cyber Security Jargons by Appknox
Cyberattacks are getting common and their impact is quite severe. Security breaches are no longer limited to a few large tech companies. Cybercriminals have rapidly altered tactics and started targeting several Small and Medium Enterprises (SMEs) as well. Today, companies, big or small, are targets of ransomware, viruses, malware, bots etc. Hence, it is important to understand some of the common cybersecurity keywords or jargon.
How mob programming and sourcing jams activate collaboration at Detectify
Collaboration Rules is a company core value and at the heart of Detectify. It drives innovation and productivity in our organization, and activates our ability to build products to drive the future of internet security. Two of the methods we use for collaborating are Mob Programming in Engineering and Sourcing Jams in the Talent Acquisition team. At Detectify, collaboration is the way forward, and let’s dive into these use cases and our learnings.