Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
AIOps Studio Getting Started and User Interface Tour | Tejo Prayaga | CloudFabrix
Egnyte Expands Content Governance and Compliance Solutions for Google Workspace and Dropbox
If you’re like most companies, your teams rely on a variety of cloud apps and storage solutions to get work done and collaborate with internal and external teams. While this flexibility is great for end users, it creates enormous complexity when it comes to data security and governance. IT teams must juggle multiple administrative dashboards, permissions configurations and access control policies across apps.
Are crypto miners feeding the GPU scalper bot frenzy?
Table of Contents PC gamers have long been frustrated by the rising cost of top-performing graphics cards, fueled in part by GPU-hungry cryptocurrency miners. It’s a dream scenario for scalpers, but can it be stopped? As experts in malicious bot activity, we talk a lot about scalpers at Netacea. Our Head of Threat Research Matthew Gracey-McMinn has even appeared on US news channels to talk on the subject.
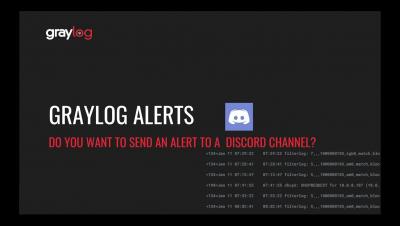
How to Send A Graylog Alert to Discord
SecurityScorecard Announces Next Generation Security Signals Capability to Deliver On-Demand Reporting and Accelerate Threat Response
The importance of behavior analytics in your organization's cybersecurity
Collin’s dictionary defines “behavior pattern” as a recurrent way of acting by an individual or group toward a given object or in a given situation. Analyzing and understanding the behavior patterns of individuals has proven to provide in-depth solutions to problems in different walks of life, including cybersecurity.
Automated Penetration Testing vs. Manual Penetration Testing
Many businesses are running remotely as a result of the latest COVID-19 pandemic. The 'new normal' has expanded the market for digital transformation initiatives and cloud migration strategies. However, according to Verizon's 2020 Data Breach Investigations Report, cybercriminals are taking advantage of enterprises' desperate digital transformation initiatives by developing new ways to target and exploit their web applications.
Mitigating and remediating intent-based Android security vulnerabilities
In previous posts we explored the potential for intent-based Android security vulnerabilities and then used Snyk Code to find exploits in popular apps on the Google Play store. If you know Snyk, you also know there’s no way we can just point out vulnerabilities and not recommend fixes. Analyzing such an extensive dataset enabled us to review a lot of code.