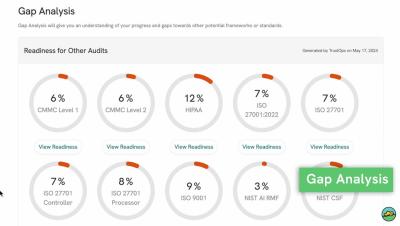
Fraud Alert vs Credit Freeze: Which One Should I Use?
Both fraud alerts and credit freezes are free of charge, but there are some differences between the two you should be aware of if you’re deciding on placing one over the other. Both fraud alerts and credit freezes are meant to protect you from identity theft and fraud, however, fraud alerts add an extra layer of verification and only last a year, whereas credit freezes prevent new credit from being opened and don’t expire.