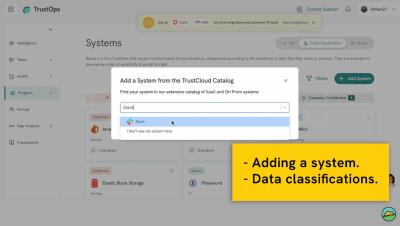
What are the Components of an Excellent Offensive Security Program
In the dynamic world of cybersecurity, creating an effective offensive security program is paramount for organizations seeking to proactively identify and mitigate potential threats. An offensive security program encompasses a suite of strategic components designed to test and strengthen an organization's defenses. An effective offensive security program includes various components, such as penetration testing, red/purple teaming, managed vulnerability scanning, and bug bounty programs, to name a few.