Why Standard Approaches to Cloud Data Security Fall Short
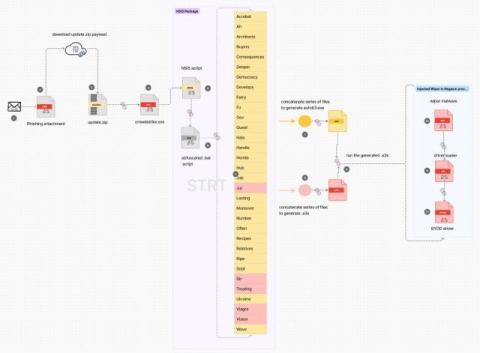
Prioritizing cloud security looks different for every business. However, many businesses migrating to the cloud rely on conventional data security methods, including built-in tools from cloud providers and ad hoc measures. Unfortunately, these traditional approaches often fall short, leaving critical gaps in protection and hindering true cloud-powered innovation. Ensuring secure cloud services are multifaceted, let’s dive deeper into the impacts, strategies, and solutions.