Keeper 101 - How to Create Your Keeper Account on iOS
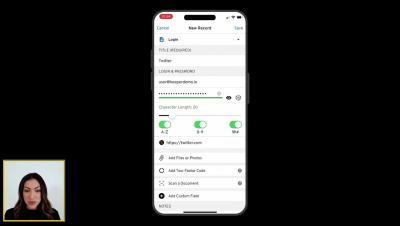
Signing up for Keeper's iOS mobile app is easy. Simply visit the App Store on your device, search for Keeper, and install “Keeper Password Manager”. Once the download is complete, tap Open to launch Keeper. Tap Create Account to get started. Enter your email address and tap Next. You will be prompted to set and confirm a master password. Don’t forget your master password! Since this password will unlock all of your other passwords in your Keeper Vault, it is critical that you set a strong master password using upper and lowercase letters, numbers and symbols.