Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SBOM
(SBOM) Creation of your Software Bill of Materials
3 Ways a Dynamic SBOM Enhances Security
In a previous post, we described why a software bill of materials (SBOM) needs to be dynamic in order to be valuable for organizations. One of the biggest sources of that value is the enhanced security that dynamic SBOMs can deliver for organizations An SBOM creates a foundational data layer on which further security tools, policies and practices can be built. The U.S.
SBOMs Are Only Truly Useful if They're Dynamic
The software bill of materials (SBOM) is being widely touted as a way to ensure the security and integrity of software products. This is an accurate assessment, but not all SBOMs are created equal. Specifically, those that are dynamic are far more useful and effective than those that are not. In fact, SBOMs that are not dynamic—able to easily and automatically account for the constant change swirling around the software landscape—are of minimal use.
Generating an SBOM is just the tip of the iceberg
It has been nearly a year since the President Biden’s Executive Order 14028 catapulted Software Bills of Materials (SBOMs) from niche topic to the forefront of efforts to improve security of cyber supply chains. Since then not only have federal agencies including NIST and CISA delivered significant amounts of guidance and insight, but SBOMs have been the subject of intense debate across developer communities and beyond.
How to generate a Software Bill of Materials (SBOM) using Veracode Software Composition Analysis
How to Generate an SBOM in Veracode SCA
Emerging government regulations have driven the advancement of standards for securing software supply chains. The production of a Software Bill of Materials (SBOM) in a standard format is an increasing audit and compliance need for large organizations.
ApSsec Decoded: Is an "SBOM" a Silver Bullet for Software Supply Chain Security? | Synopsys
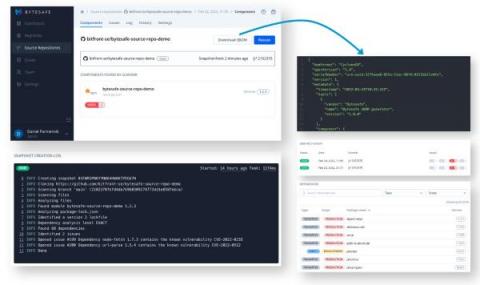
Export and Distribute SBOMs Directly From Your Git Repositories
Guest Blog by Daniel Parmenvik – CEO of bytesafe.dev For many, Software Bill of Materials (SBOMs) have changed from a manual list of assets for due diligence procedures to become an integral and automated part of software development. The ever increasing appetite for open-source software translates into a need to keep track of software assets (or open-source dependencies) for all applications, at any given point in time.
With SBOMs, Sharing is Caring
Thanks to President Biden’s Executive Order on Cybersecurity (14028) last May, Software Bills of Material (SBOMs) are now discussed by developers, security and deployment teams and even boards of businesses around the world. These “ingredients” lists for software are mandated for those selling to US Federal government and are quickly becoming an expected element of any software implementation. Rightly so.